How I could have mass uploaded from every Flickr account!
This was one of my first valid security issue on the Yahoo Bug bounty program. I wanted to write about this very specific bug because I haven’t really seen anyone reporting this kind of issue, or mess with this kinda stuff. So let’s dive right into this.
The first thing I do whenever I approach a target is try to understand it’s functionality, and where the most crucial parts of the application lie.
So while I was doing my functionality test, after like 30 minutes, I stumbled upon this Feature of Flickr, in which you can upload a picture to your account by sending an email to a specific address.
https://www.flickr.com/account/uploadbyemail/
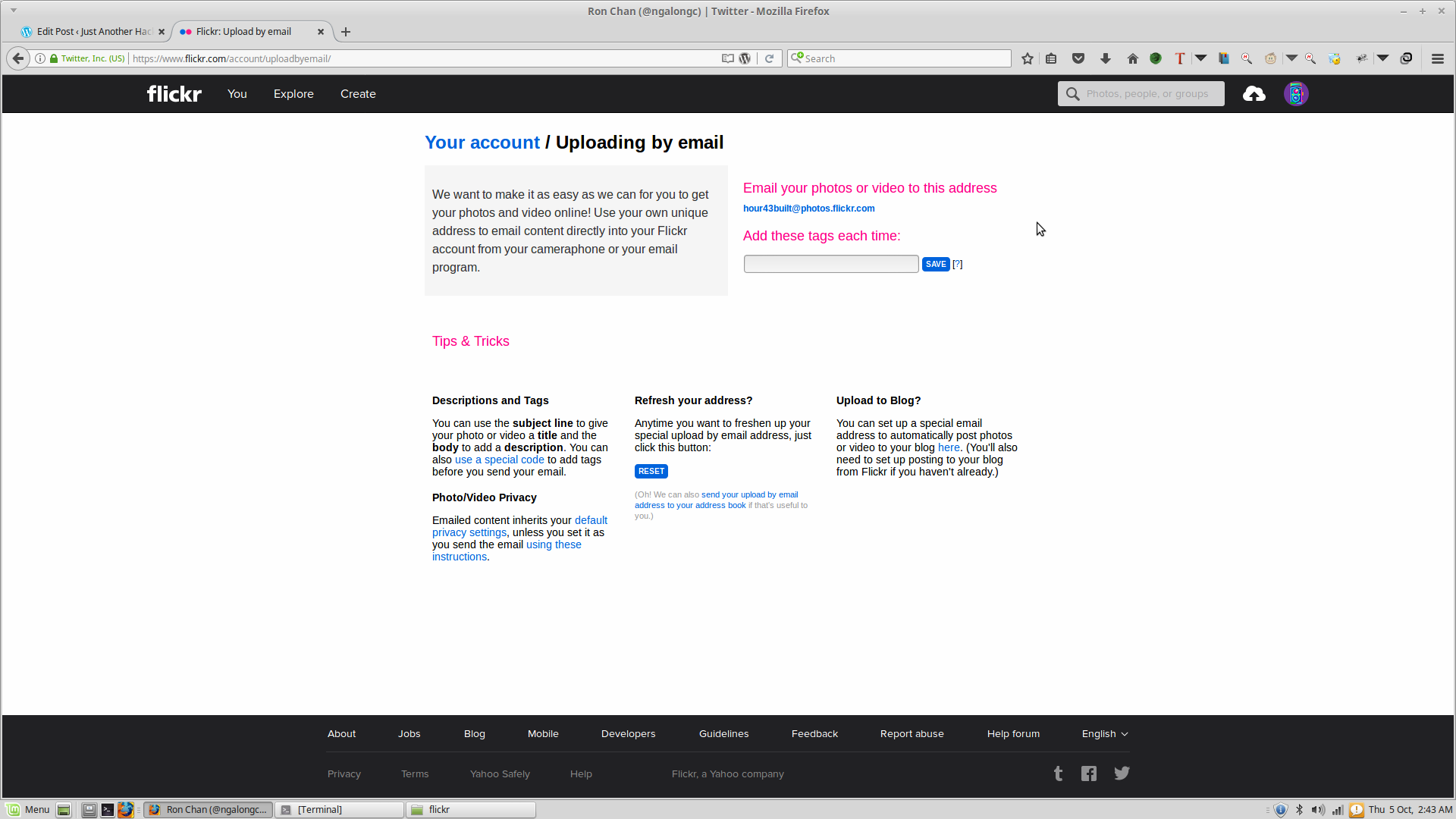
So basically this is how it works:
Flickr gives each account a unique email address, which then can be used to directly upload pictures to the account, by just sending an email with the picture as an attachment to the unique email address given by Flickr.
So I got thinking, what if an attacker somehow figures out what email is used with each account, then he would be upload pictures/videos in the victims account without any restriction, and he wouldn’t even need a password.
Then I began formulating strategies about where this email address could be leaked, but I couldn’t find any request/endpoint which leaks this unique email address.
Then there was this button which allowed you to change your email address and get a new one. I clicked it and I instantly got a new address. Then I did it again, and again, and again… and I finally saw a pattern. The email returned by Flickr had some specific properties, and it was in this form.
<Random dictionary word><Random number 0-100><Random Dictionary word>@photos.flickr.com
Another thing I noticed was that the length of the Dictionary word was always less than 6 characters. So I thought, what if we could Bruteforce this email address(Since it contained dictionary words). But I didn’t really expect it to work because I thought they’d be using some pretty big dictionary with more than a million words, and that would make bruteforce not really a viable option. But I still decided to give it a try.
I spun up a quick python script which would constantly change my email address and then write it to a file.
Then I just ran the script overnight, and by morning, I had almost 20,000 email address returned by Flickr. Then I spun up another quick script to sort through them and show me some statistics. This was the output
$ python flick.py
Total emails loaded ==> 23692
Total unique words found ==> 935
1 word(s) has/have been repeated 128 times
1 word(s) has/have been repeated 29 times
1 word(s) has/have been repeated 30 times
2 word(s) has/have been repeated 31 times
1 word(s) has/have been repeated 32 times
3 word(s) has/have been repeated 33 times
4 word(s) has/have been repeated 34 times
4 word(s) has/have been repeated 35 times
6 word(s) has/have been repeated 36 times
13 word(s) has/have been repeated 37 times
12 word(s) has/have been repeated 38 times
18 word(s) has/have been repeated 39 times
31 word(s) has/have been repeated 40 times
32 word(s) has/have been repeated 41 times
31 word(s) has/have been repeated 42 times
22 word(s) has/have been repeated 43 times
38 word(s) has/have been repeated 44 times
44 word(s) has/have been repeated 45 times
37 word(s) has/have been repeated 46 times
61 word(s) has/have been repeated 47 times
43 word(s) has/have been repeated 48 times
48 word(s) has/have been repeated 49 times
50 word(s) has/have been repeated 50 times
43 word(s) has/have been repeated 51 times
56 word(s) has/have been repeated 52 times
50 word(s) has/have been repeated 53 times
34 word(s) has/have been repeated 54 times
30 word(s) has/have been repeated 55 times
35 word(s) has/have been repeated 56 times
42 word(s) has/have been repeated 57 times
.........
This actually Blew my mind. Out of 23,000 email address, only 935 unique words were used. This was that “WHAAAATTT!!!” moment.
Now for some maths, considering Flickr’s dictionary only has 935 unique words, the amount of permutations it can generate from those words is 935 * 935 * 100, the 100 for the random number between the two words, and 935 * 935 for two unique words it uses from its dictionary.
>>> 935 * 935 * 100
87422500
That is almost 87.5 million. Now for some statistics, Flickr has almost 51 million registered users, and each user has their own unique email address.
So now if i start generating email addresses myself from the permutations of the dictionary words I enumerated, one out of two emails I generate would be a valid Flickr email. That is more than a 50% chance of generating a valid email in each generation.
Now we can attack this Scenario in a very efficient way, we could generate all the 87.5 million emails, and then just write a script which would mass mail each one of those emails. Flickr doesn’t verify what address the email came from, so we can send emails from any random address and they would still get uploaded.
It won’t even take more than 3 hours to send 87.5 million emails using a multithreaded script and some power. And we can even send a single email to multiple addresses by CC/BCC, which would further reduce the amounts of emails to send.
Now by exploiting this, an attacker can easily upload pictures and videos from any Flickr account. I reported it as soon as a i verified this, and it was marked as P1 as soon as it was triaged. Yahoo fixed it quickly and i was rewarded a nice bounty :)
Thanks for reading, Please leave your comments below if you’ve any questions. Jazzy
UPDATE: Just got a message from the yahoo security team that this feature is not enabled by default. You need to visit the “Upload By Email” Page to enable. So only some percent of Flickr users were affected

